Shodan: The “Search Engine for Hackers” Exploring the Internet’s Connected Devices
1. What Is It?
Shodan is a search engine that indexes information about internet-connected devices—ranging from servers, routers, and webcams to industrial control systems (ICS). Nicknamed “the search engine for hackers,” Shodan scans the public internet, gathering details like open ports, banners, and device metadata for security analysis or research purposes.
Which Problem Does It Solve? Traditional web search engines (like Google) primarily index websites, but Shodan dives deeper, cataloging the underlying infrastructure of the internet. For security researchers and network administrators, it’s a powerful tool to discover unsecured devices, misconfigurations, or potential vulnerabilities—aligning with MyDigitalFortress ideals of transparency and proactive defense.
2. Technical Foundations
Global Port Scanning & Banners
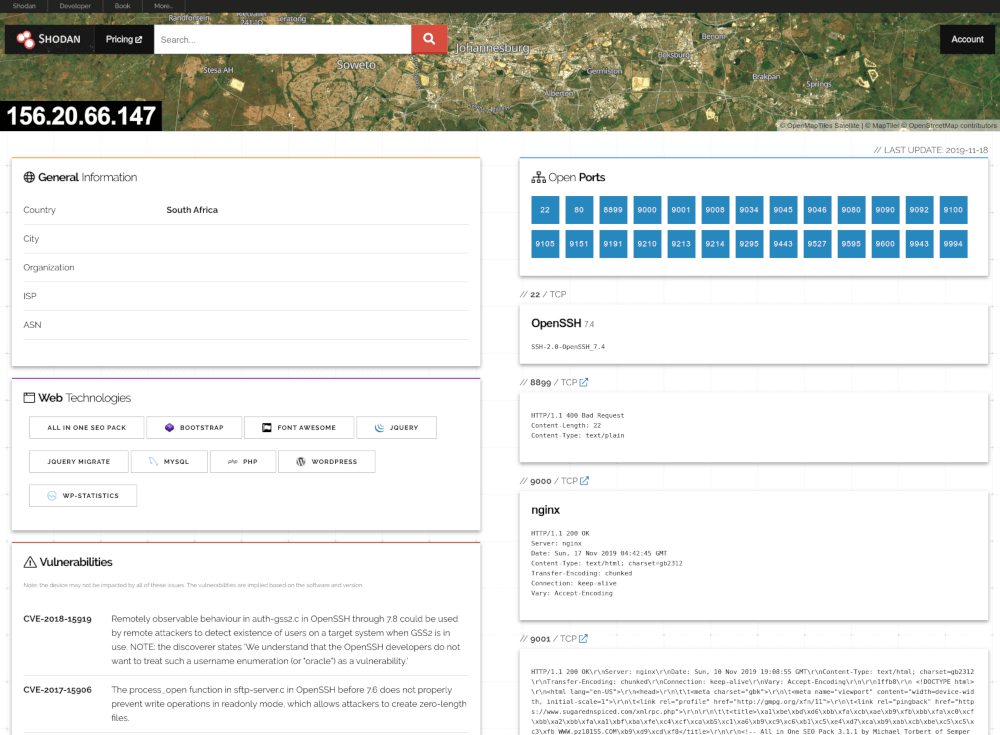
Shodan’s crawlers scan the IPv4 (and sometimes IPv6) address space, probing common ports (e.g., 80, 443, 22, 21) and collecting service banners or SSL certificates. It stores these banners, which often contain server software, versions, or self-identifying text. This data is indexed in a searchable database, letting users query strings like “Apache server country:US” or “SSL version: outdated.”
With Shodan Explore, one can discover trending vulnerabilities, popular device types, or interesting misconfigurations, all derived from these scanned banners. In many ways, it’s a deeper, more technical snapshot of the internet’s exposed services.
API Access & Python Integration
Beyond the web interface, Shodan provides an API for developers to automate searches, integrate results into SIEM solutions, or enrich cybersecurity workflows. They also maintain a Python library , enabling scripts to query Shodan for open ports, device metadata, or even create real-time monitoring dashboards for exposed assets.
This emphasis on accessible APIs cements Shodan as a powerful research platform, though it raises ethics and privacy concerns—since anyone, including malicious actors, can also systematically locate vulnerable targets.
3. Who Benefits from Shodan?
Shodan is an indispensable tool for those dedicated to strengthening cybersecurity and ensuring digital resilience—values at the heart of MyDigitalFortress. It empowers a diverse audience to proactively identify exposed services and potential vulnerabilities across their networks.
- Ethical Hackers & Security Researchers: Utilize Shodan to simulate real-world attack scenarios and assess vulnerabilities, ensuring systems are robust against emerging threats.
- Cyber Defenders & System Administrators: Leverage Shodan’s comprehensive scanning data to continuously monitor and secure their networks, preventing inadvertent exposures before they can be exploited.
- Academic & Industry Analysts: Study global device distribution trends and security anomalies, contributing critical insights that help shape future cybersecurity best practices.
- Law Enforcement & CERT Teams: Investigate malicious activities by tracking botnets, command-and-control infrastructures, and unauthorized access points, supporting proactive threat mitigation.
While casual users might only explore Shodan for personal curiosity—like scanning their IP for exposed services—the MyDigitalFortress approach underscores responsible use. We advocate using these insights to bolster security measures and raise awareness about potential digital risks, ensuring that every scan contributes to building a safer, more secure online environment.
4. Use Cases & Real-World Adventures
- Finding Hidden Bugs: Imagine an online detective on the hunt for clues. A smart security expert might search for older versions of software—like an outdated phpMyAdmin installation—that could have security flaws. This helps uncover hidden bugs and encourages updates to keep systems safe.
- Watchdog Mode: CERT teams (or Computer Emergency Response Teams) are cybersecurity professionals who continuously monitor networks to detect and respond to threats. You can think of them much like a neighborhood watch, or your friendly neighborhood protectors. They keep an eye on everything—even unexpected items like your home smart devices—to alert you if something looks fishy, helping identify potential issues before they turn into major problems.
- Gadget Treasure Hunt: For researchers, scanning the internet becomes like going on a digital treasure hunt. They search for devices like unsecured webcams or default-password gadgets. It’s about finding things that are visible online without the usual barriers, all in the name of boosting security awareness.
- Home Turf Check: Just like keeping an eye on your neighborhood, network admins check their own IP ranges to make sure nothing unexpected is open to the world. It’s a proactive way to prevent unwanted visitors from taking advantage of overlooked security gaps.
5. Pros & Cons
Pros
- Comprehensive Internet-Wide Data: Shodan continuously scans public IPv4 (and sometimes IPv6) networks to aggregate open ports, service banners, and SSL certificate details.
- Powerful Search Syntax & API: Offers advanced search operators (e.g., port:, country:, org:) and programmatic access via a REST API and Python library, enabling fine-grained queries.
- Valuable Security Insights: Aggregated data reveals misconfigured services and outdated software, helping identify vulnerabilities on a global scale.
- Frequent Updates & Community Tools: Regular, continuous scans combined with community-contributed tools and third-party integrations enrich Shodan’s usefulness.
Cons
- Potential for Malicious Use: The same data that aids defensive security can be exploited by attackers to locate unpatched or vulnerable devices.
- Privacy & Ethical Concerns: Although Shodan collects publicly available information, its data acquisition methods can raise privacy or legal issues. Confirm that the vendor offers clear guidance and compliance measures for regulated environments.
- Subscription Costs for Advanced Features: Enhanced capabilities—such as full historical data, real-time alerts, and increased API call limits—require a paid subscription.
- Skewed Focus on Public IPv4: Shodan primarily indexes publicly accessible IPv4 addresses, which can leave out devices on private networks or using IPv6.
6. Getting Started
Ready to explore Shodan? Here’s a brief how-to:
- Create a Shodan Account: Sign up at https://account.shodan.io/register. A free tier allows basic searches; advanced queries need a paid subscription.
- Run Simple Searches: Try basic queries like “ssh”, “apache”, or “country:US port:80” to see exposed devices.
- Explore Filters & Syntax: The Shodan Help Center details operators (e.g., port:, org:, ssl:, etc.).
- Use the Shodan API: Install the Python library or integrate via REST endpoints. Acquire an API key for authorized calls.
- Practice Ethical Usage: Restrict searches to assets you own or have permission to assess. Refer to local laws and usage policies—MyDigitalFortress stance on legal, ethical scanning applies here.
7. Conclusion & Next Steps
Shodan is a powerful, unique search engine mapping the world’s connected devices by scanning open ports and grabbing service banners. From a security vantage point, it’s invaluable for identifying vulnerabilities or misconfigurations. Yet, it also highlights how easily accessible these exposed devices can be—a sobering reminder of the need for robust cyber hygiene and continuous monitoring.
At MyDigitalFortress, we stress that knowledge is a double-edged sword: used responsibly, Shodan promotes proactive defense; used nefariously, it aids malicious actors. Balancing transparency, legality, and privacy is paramount when leveraging internet-wide scanning data.
Next steps? Sign up for Shodan and attempt a basic audit of your own IP range. Explore Shodan’s advanced query capabilities, or experiment with the API for real-time threat alerts. Just remember: use it ethically—and if you spot major issues on public devices, consider responsibly disclosing them to owners or relevant authorities.





